Configuring Single Sign-on (SSO) with SAML Authentication
![]() See a video on Configuring Single Sign-on with SAML Authentication
See a video on Configuring Single Sign-on with SAML Authentication
![]() See a video on Configuring Laserfiche Directory Server for SAML Authentication with Okta
See a video on Configuring Laserfiche Directory Server for SAML Authentication with Okta
![]() See a video on Configuring Laserfiche Directory Server for SAML Authentication with Shibboleth
See a video on Configuring Laserfiche Directory Server for SAML Authentication with Shibboleth
- After you've specified the name, identity provider type, and host for your new SAML identity provider, select Enable SAML authentication.
- For quick configuration, import a metadata file for the SAML identity provider. Directory Server will attempt to automatically extract the issuer, endpoint, endpoint binding type, and certificate values from the metadata file.
Note: You can also manually enter values for Issuer, Endpoint, and Endpoint binding type, and manually select a certificate.
- For the Name ID format, the default value is:
urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified
- For the Authentication context, specify the appropriate authentication method for your SAML identity provider. For example, if the SAML identity provider requires password authentication, the default value is:
urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport
If the identity provider requires certificate authentication, the value is:
urn:oasis:names:tc:SAML:2.0:ac:classes:X509
If the identity provider can require more than one authentication method, the value should be:
urn:oasis:names:tc:SAML:2.0:ac:classes:unspecified
Note: See the Authentication Context for the OASIS Security Assertion Markup Language (SAML) V2.0 standards document for a list of authentication context classes.
- Optional: Turn on the Always require re-authentication option to configure Directory Server to include the ForceAuthn="true" parameter in SAML requests. When set, the Identity Provider may require a user to sign in even if they have already signed in previously and their session is still valid. Note that not all identity providers support this option. You should verify that your SAML identity provider supports this option before enabling this option.
Note: It is recommended that administrators configure authentication policies within the SAML identity provider (i.e., Microsoft Entra ID, Okta, etc.) rather than within a SAML service provider (i.e., Laserfiche Directory Server). Identity provider authentication policies often provide useful conditionals, including risk-based ones.
- Optional: Depending on whether the selected certificate is located in the trusted root store, you can choose to Ignore certificate chain validation. By default, the issuer chain list must contain at least one issuer in the machine's root trusted store.
Warning: Laserfiche strongly recommends against enabling this option. This option is provided for troubleshooting purposes, as enabling this option can potentially weaken the security pattern. It is recommended to install all necessary certificate(s) in the machine "Trusted Root Certification Authorities" and "Intermediate Certification Authorities" certificate stores. For self-signed certificates, install the certificate itself in the "Trusted Root Certification Authorities" store to pass chain validation.
- Optional: If you turn on the Sign authentication request option, you must provide the thumbprint (without spaces) of a certificate that satisfies the following requirements:
- The certificate must contain the private key for signing and the Directory Server service user must have read access to the private key. For instructions on setting private key permissions, see the following Laserfiche Knowledge Base article: https://support.laserfiche.com/kb/1014366.
- The certificate must be trusted by the Laserfiche Directory Server computer and pass certificate chain validation. You can check the trust status by opening the certificate, selecting the Certification Path tab, selecting each certificate in the chain, and verifying each has a certificate status of OK. If any certificates in the chain are not trusted, view the certificate and install the certificate in the appropriate certificate stores ("Trusted Root Certification Authorities" for root certificates and "Intermediate Certification Authorities" for intermediate certificates).
- The certificate must use the RSA signature algorithm.
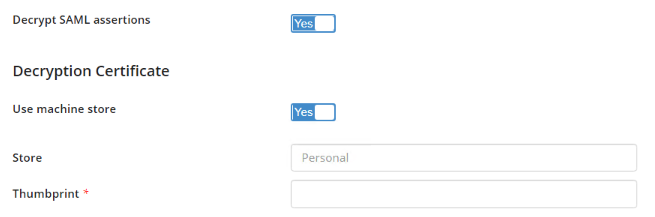
- Optional: For Directory Server 10.4.3 or later, turn on Decrypt SAML assertions and provide decryption certificate information if your SAML identity provider is configured for encrypted SAML tokens. When enabled, this option means that Directory Server will only accept encrypted tokens from this identity provider. In addition to providing the thumbprint, you must also satisfy the following requirements:
- The Directory Server service user must have read permissions to the private key of the certificate.
- The SAML provider must include the signature in the encrypted assertion.
- Toggle Use machine store to Yes.
- The certificate is located in the current machine Personal store.
- Certificate must be trusted by the Laserfiche Directory Server computer. This can be done by adding the certificate, a copy of the certificate, or one of the issuer certificates to a trusted store.
- Store field is left at its default value Personal.
- Directory Server 10.3.1 or later: If you use a SAML discovery service, use the Hide identity provider button on sign-in page option to remove the default single-sign on button on the Directory Server sign-in page.