Configuring Single Logout (SLO) with SAML Authentication
When configured, Laserfiche Directory Server will end active application sessions upon receiving a logout request from a SAML provider. When applicable, SAML providers can also end their active sessions upon receiving a logout request initiated by Laserfiche Directory Server. (Only available for certain SAML Identity Providers)
Identity Provider Prerequisites
The SAML 2.0 specification identifies two types of single logout requests, depending on who initiates the requests:
- Service provider (SP-initiated): Directory Server is the service provider.
- Identity Provider (IdP-initiated): SAML Identity Providers (e.g., AD FS, Microsoft Entra ID, and Okta)
- AD FS and Microsoft Entra ID support both SP-initiated and IdP-initiated single logout requests.
- Okta supports SP-initiated single logout requests. (Okta support for IdP-initiated single log out requests is marked as "Early Access.")
Configure the identity provider for single logout:
- Entra ID: https://learn.microsoft.com/en-us/entra/identity-platform/single-sign-out-saml-protocol
- Okta: https://help.okta.com/en-us/Content/Topics/Apps/Apps_Single_Logout.htm
Directory Server Configuration
- After configuring Single Sign-on (SSO) with SAML Authentication, locate the
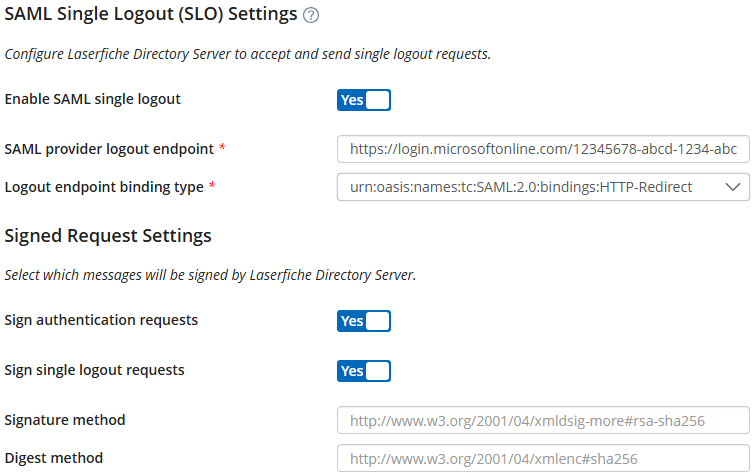
 SAML Single Logout (SLO) Settings section and select Enable SAML single logout.
SAML Single Logout (SLO) Settings section and select Enable SAML single logout.
- Either manually set the SAML provider logout endpoint and Logout endpoint binding type according to your appropriate SAML Identity provider or import a metadata file for your SAML identity provider. With a metadata file, Directory Server will attempt to automatically extract the appropriate endpoint value and binding type from the metadata file.
Note: Microsoft Entra ID currently supports redirect binding, see https://learn.microsoft.com/en-us/entra/identity-platform/single-sign-out-saml-protocol.
- Install the SAML certificate(s) in the Directory Server machine's "Trusted People" local certificate store. The SAML certificate(s) can be downloaded from your SAML identity provider.
- Optional: If you turn on the Sign single logout requests option, you must provide the thumbprint (without spaces) of a certificate that satisfies the following requirements:
- The certificate must contain the private key for signing and the Directory Server service user must have read access to the private key. For instructions on setting private key permissions, see Laserfiche Knowledge Base article 1014366.
- The certificate must be trusted by the Laserfiche Directory Server computer and pass certificate chain validation. You can check the trust status by opening the certificate, selecting the Certification Path tab, selecting each certificate in the chain, and verifying each has a certificate status of OK. If any certificates in the chain are not trusted, view the certificate and install the certificate in the appropriate certificate stores ("Trusted Root Certification Authorities" for root certificates and "Intermediate Certification Authorities" for intermediate certificates).
- The certificate must use the RSA signature algorithm.
- On the computer hosting the Directory Server Security Token Service (STS), open the STS configuration site, by default, the address is: https://localhost/LFDSSTS/configuration
- Add the domain of the SAML SLO endpoint for your identity provider to the list of Allowed iframe hosts.
- For example, for a Microsoft Entra ID sample endpoint of https://login.microsoftonline.com/{guid}/saml2, add https://login.microsoftonline.com to the Allowed iframe hosts list.
Additional References