Hosting Forms In A Perimeter Network (DMZ)
Introduction
This document provides an overview of configuring Laserfiche Forms in a perimeter network or DMZ. It outlines the following ways to configure Forms for secure access:
- A standard configuration with two Forms servers and public access to Forms. This involves having one Forms server in the DMZ and another Forms server in the internal network. In the internal network, you can have either a Laserfiche Server with an Active Directory server, or a Laserfiche Directory Server with a Security Token Service (STS) instance.
- A version of the standard configuration, but with an additional STS instance in the DMZ. This allows users accessing Forms through a public portal to authenticate to the STS instance in the DMZ, meaning that you do not have to grant these users access to the internal network. This configuration is only possible if Forms authentication goes through Laserfiche Directory Server.
- A high-security variation on the standard configuration. The main difference with 1) is that there are two SQL Servers rather than one. One SQL Server is in the DMZ and the other is in the internal network.
- A configuration with only one Forms server, with an STS instance in the DMZ. This configuration is only possible if Forms authentication goes through Laserfiche Directory Server.
Two Options for Configuration
Multi-Server Configuration Utility
You can use the Multi-Server Configuration Utility to simplify the server configuration. Depending on your needs, some manual configuration my be required.
Manual Configuration
If required, the instructions for Manually Configuring Forms in a DMZ are available. This guide provides complete step-by-step instructions for editing the configuration files.
Note: When configuring the DMZ, you may need the hardware fingerprint of your machine. You can retrieve the hardware fingerprint using the Hardware Fingerprint Utility on the Forms server machine. A copy of this utility (showhwfp.exe) can be found in the Laserfiche Server installation directory, which by default is C:\Program Files\Laserfiche\Server.
Licensing
Both Forms Essentials and Forms Professional allow for multiple Forms servers. All your Forms servers should have a Forms license of either type. In addition, you will need a Forms portal license to make forms on the DMZ server available to the public. After adding a Forms portal license, you can then make any form public.
Standard DMZ Configuration: Two Forms Servers, One SQL Server
In the standard configuration, you will install two instances of the Laserfiche Forms server: The primary instance in the internal network, and a second publicly accessible instance in the DMZ. Both instances authenticate to either a Laserfiche Server or a Directory Server STS instance in the internal network. To configure authentication to an STS instance in the DMZ, see the next configuration.
The publicly accessible Forms server located in the DMZ will be able to serve forms to site visitors but will not perform any of the business logic associated with a Forms process. This is because you will disable the routing service for the Forms server located in the DMZ. The internal Forms server is a full installation of Forms. Both Forms servers will point to the same Forms database on SQL Server, located in the internal network.
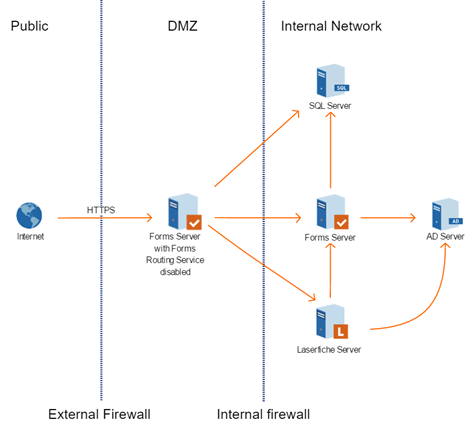
The DMZ Forms server must be able to communicate with the internal Forms server and the internal SQL Server instance hosting the Forms database. Depending on the authentication method, the DMZ Forms server must also be able to communicate with either a Laserfiche Server instance or a Laserfiche Directory Server instance. The diagram shows a setup with Laserfiche Server authentication and an Active Directory (AD) server. With Laserfiche Directory Server, you would have Laserfiche Directory Server and its STS in the internal network, instead of the AD server.
Click here for instructions using the utility, or here for manual configuration instructions.
Two Forms Servers with Two STS Instances
This configuration works only if you are using Laserfiche Directory Server. It is identical to the standard configuration, except that the DMZ Forms server authenticates to an STS instance in the DMZ, while there is a separate STS instance in the internal network for the primary Forms server to authenticate to. To accommodate having an STS instance on a different computer from the Directory Server computer, we must change the endpoints in the DMZ Forms server.
Click here for instructions using the utility, or here for manual configuration instructions.
Note: For the STS instance in the DMZ to authenticate to the Directory Server in the internal network, the DMZ server must have a valid SSL certificate.
High-Security Variation: Two Forms Servers, Two SQL Servers
This configuration is like the standard configuration, except that there are two SQL Server instances rather than one. An additional copy of the Forms database is in the DMZ with the DMZ Forms server. The DMZ Forms server does not communicate with the Forms SQL Server on the internal network. The SQL database in the DMZ stores the blank starting form definitions but is scrubbed of process data.
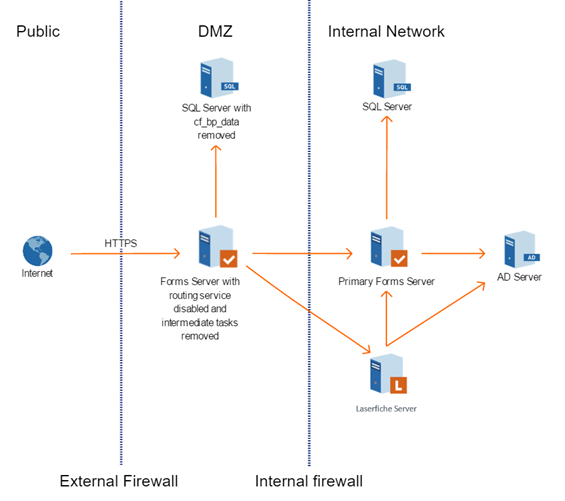
In this configuration, a public user accessing Forms through the internet can only submit a form (including file uploads) or start a process. They cannot do anything else through a public connection.
This configuration is possible with both Laserfiche Server authentication and Laserfiche Directory Server authentication.
Click here for instructions using the utility, or here for manual configuration instructions.
One Forms Server in DMZ
This configuration uses only one Forms server, located in the DMZ. A Laserfiche Directory Server STS instance should be installed in the DMZ. Laserfiche Directory Server and the Forms SQL Server should be installed in the internal network.
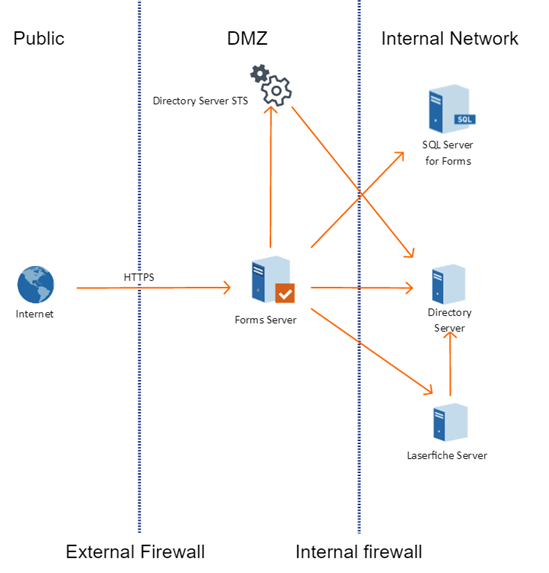
Click here for instructions using the utility, or here for manual configuration instructions.
Note: In order for the STS instance in the DMZ to authenticate to the Directory Server in the internal network, the DMZ server must have a valid certificate.